Maritime and logistics companies in South and Southeast Asia, the Middle East, and Africa are being targeted by an advanced persistent threat (APT) group known as SideWinder.
In 2024, Kaspersky observed attacks in several countries, including Bangladesh, Cambodia, Djibouti, Egypt, the United Arab Emirates, and Vietnam. The group has also targeted nuclear power plants and nuclear energy infrastructure in South Asia and Africa, as well as companies in the telecommunications, consulting, IT services, real estate, and hospitality sectors.
SideWinder has expanded its reach, targeting diplomatic entities in Afghanistan, Algeria, Bulgaria, China, India, the Maldives, Rwanda, Saudi Arabia, Turkey, and Uganda. Notably, the targeting of India is significant, as the threat actor was previously suspected to be of Indian origin.
According to researchers Giampaolo Dedola and Vasily Berdnikov, “SideWinder continually updates its toolsets, evades security software detections, and extends its persistence on compromised networks, making it a highly advanced and dangerous adversary.”
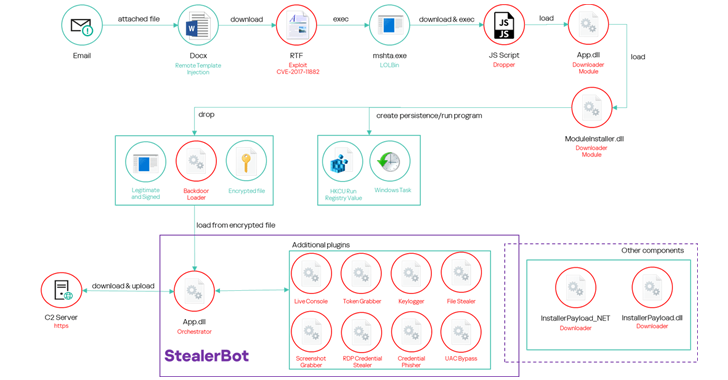
SideWinder was previously analyzed by Kaspersky in October 2024, which documented the threat actor’s use of a modular post-exploitation toolkit called StealerBot to capture sensitive information from compromised hosts. The group’s targeting of the maritime sector was also highlighted by BlackBerry in July 2024.
The latest attack chains involve spear-phishing emails with booby-trapped documents that exploit a known vulnerability in Microsoft Office Equation Editor (CVE-2017-11882) to activate a multi-stage sequence, ultimately launching StealerBot.
Some of the lure documents used by SideWinder are related to nuclear power plants and nuclear energy agencies, while others reference maritime infrastructures and port authorities.
Kaspersky notes that SideWinder “constantly monitors detections of their toolset by security solutions” and responds by generating new and modified versions of the malware, often in under five hours.
If behavioral detections occur, the group changes its techniques to maintain persistence and load components, and also changes the names and paths of its malicious files.