Cybersecurity experts have identified a new spear-phishing campaign that leverages a legitimate remote access tool called Netbird to target Chief Financial Officers (CFOs) and financial executives at various organizations across Europe, Africa, Canada, the Middle East, and South Asia.
According to Trellix researcher Srini Seethapathy, “the attackers aim to deploy NetBird, a legitimate wireguard-based remote access tool, on the victim’s computer” in a multi-stage phishing operation. Seethapathy’s analysis reveals the intricacies of the attack.
The campaign, first detected in mid-May 2025, has not been linked to a specific threat actor or group.
The initial attack vector is a phishing email that impersonates a recruiter from Rothschild & Co., claiming to offer a “strategic opportunity” with the company. The email is designed to trick recipients into opening a purported PDF attachment, which is actually a phishing link redirecting them to a Firebase app-hosted URL.
What’s notable about the infection is that the real redirect URL is stored in encrypted form on the page and can only be accessed after the victim solves a CAPTCHA verification check, ultimately leading to the download of a ZIP archive.
Seethapathy explains that “solving the puzzle executes a JavaScript function that decrypts it with a hard-coded key and redirects the user to the decrypted link.” This tactic allows attackers to evade detection by using custom CAPTCHA gates, which are becoming increasingly popular.
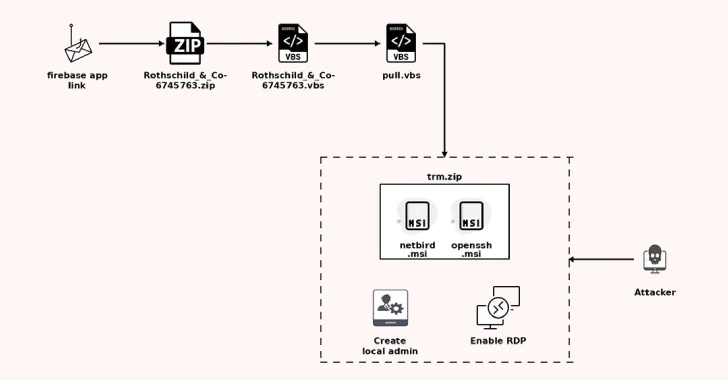
The ZIP archive contains a Visual Basic Script (VBScript) responsible for retrieving a next-stage VBScript from an external server and launching it via “wscript.exe.” The second-stage VBScript downloader then fetches another payload from the same server, renames it to “trm.zip,” and extracts two MSI files from i
Source Link