Here is the rewritten content:
The Computer Emergency Response Team of Ukraine (CERT-UA) has issued a warning regarding renewed activity from an organized criminal group, tracked as UAC-0173, which involves infecting computers with a remote access trojan known as DCRat (also referred to as DarkCrystal RAT).
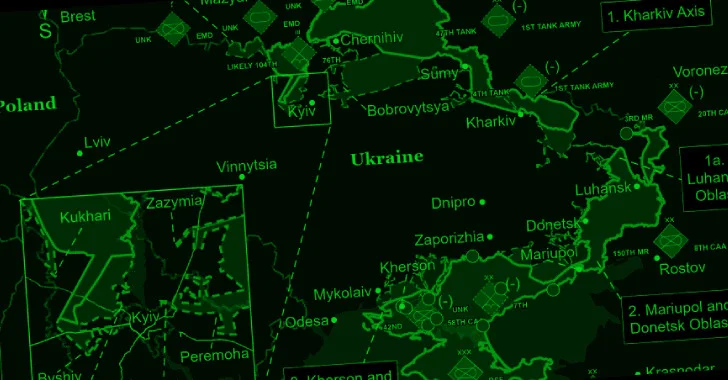
According to the Ukrainian cybersecurity authority, the latest attack wave began in mid-January 2025 and is designed to target the Notary of Ukraine.
The infection chain utilizes phishing emails that claim to be sent on behalf of the Ministry of Justice of Ukraine, prompting recipients to download an executable file. Upon launch, this file leads to the deployment of the DCRat malware, which is hosted in Cloudflare’s R2 cloud storage service.
Following the initial compromise, the attackers install additional tools, including RDPWRAPPER, which enables parallel RDP sessions. In combination with the BORE utility, this allows them to establish RDP connections from the internet directly to the computer, as stated by CERT-UA in their report.
The attacks also involve the use of other tools and malware families, such as FIDDLER for intercepting authentication data, NMAP for network scanning, and XWorm for stealing sensitive data, including credentials and clipboard content.
Furthermore, the compromised systems are utilized to draft and send malicious emails using the SENDMAIL console utility, allowing the attackers to further propagate their attacks.
This development comes shortly after CERT-UA attributed a sub-cluster within the Sandworm hacking group (also known as APT44, Seashell Blizzard, and UAC-0002) to the exploitation of a now-patched security flaw in Microsoft Windows (CVE-2024-38213, CVSS score: 6.5) in the second half of 2024 via booby-trapped documents.
The attack chains involve the execution of PowerShell commands that display a decoy file while launching additional payloads in the background, including SECONDBEST (also known as EMPIREPAST), SPARK, and a Golang loader named CROOKBAG.
The activity, attributed to UAC-0212, targeted supplier companies from Serbia, the Czech Republic, and Ukraine between July 2024 and February 2025, with some attacks recorded against over two dozen Ukrainian enterprises specializing in automated process control systems (ACST), electrical works, and freight transportation.
Some of these attacks have been documented by StrikeReady Labs and Microsoft, with the latter tracking the threat group under the moniker BadPilot.