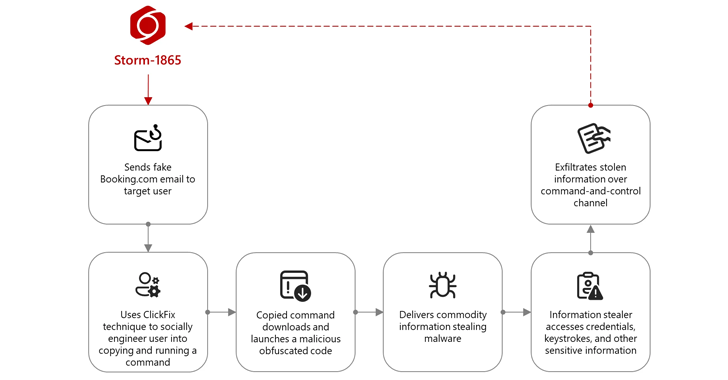
Microsoft has shed light on an ongoing phishing campaign, known as Storm-1865, that targets the hospitality sector by impersonating the online travel agency Booking.com. The attackers utilize a social engineering technique called ClickFix to deliver malware designed to steal credentials.
This campaign, which began in December 2024, aims to commit financial fraud and theft. It primarily targets individuals in the hospitality industry in various regions, including North America, Oceania, South and Southeast Asia, and Europe, who are likely to work with Booking.com. The attackers send fake emails purporting to be from Booking.com, which is a tactic that has been observed in other phishing campaigns.
According to Microsoft, the ClickFix technique has become increasingly popular in recent months, as it tricks users into executing malware by presenting a non-existent error and providing instructions to fix it. The technique was first detected in the wild in October 2023 and has been adopted by various threat actors, including nation-state groups.
The Storm-1865 campaign starts with a malicious email sent to a targeted individual about a negative review on Booking.com, requesting their feedback. The email contains a link or a PDF attachment that appears to direct the recipient to the Booking.com website. However, clicking on the link leads to a fake CAPTCHA verification page overlaid on a background designed to mimic a legitimate Booking.com page, aiming to create a false sense of security.
The fake CAPTCHA page employs the ClickFix technique to download the malicious payload. The technique instructs the user to use a keyboard shortcut to open a Windows Run window, paste, and launch a command that the webpage adds to the clipboard. This command uses the legitimate mshta.exe binary to drop the next-stage payload, which includes various commodity malware families.
Microsoft observed that Storm-1865 previously targeted buyers using e-commerce platforms with phishing messages leading to fraudulent payment web pages. The incorporation of the ClickFix technique represents a tactical evolution designed to evade conventional security measures against phishing and malware.
Group-IB noted that the ClickFix technique capitalizes on human behavior, presenting a plausible solution to a perceived problem, which shifts the burden of execution onto the user and effectively sidesteps many automated defenses. The technique has been adopted by various cybercriminals and APT groups, underscoring its effectiveness and low technical barrier.
Other campaigns have leveraged malvertising, SEO poisoning, GitHub issues, and spamming forums or social media sites with links to ClickFix pages. The diverse infection mechanisms of malware are further exemplified by the discovery of another campaign that uses bogus GitHub repositories featuring AI-content to deliver the malware via a loader.
The findings also include an email phishing campaign that uses invoice-related decoys to distribute an updated version of the StrelaStealer malware, which is operated by a single threat actor. The malware includes custom multi-layer obfuscation and code-flow flattening to complicate its analysis.