Security experts have discovered a new method that enables a malicious browser extension to masquerade as a legitimate installed add-on, posing a significant threat to users’ online security.
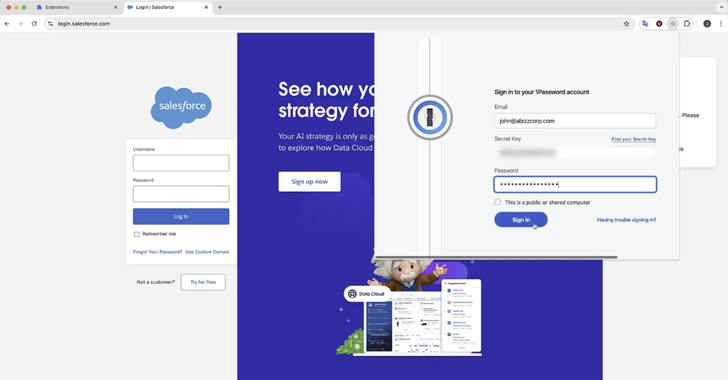
According to SquareX, “the polymorphic extensions can create an exact replica of the target’s icon, HTML popup, and workflows, and even temporarily disable the legitimate extension, making it highly convincing for victims to believe they are interacting with the real extension,” as stated in a recent report.
The stolen credentials can then be exploited by threat actors to take control of online accounts and gain unauthorized access to sensitive personal and financial information. This attack affects all Chromium-based web browsers, including Google Chrome, Microsoft Edge, Brave, Opera, and others.
The approach relies on the fact that users often pin extensions to the browser’s toolbar. In a hypothetical attack scenario, threat actors could publish a polymorphic extension to the Chrome Web Store (or any extension marketplace) and disguise it as a utility, avoiding detection.
While the add-on provides the advertised functionality to avoid raising suspicions, it secretly activates malicious features by scanning for specific target extensions using a technique called web resource hitting, allowing it to identify potential targets.
Once a suitable target extension is identified, the attack progresses to the next stage, transforming the rogue extension into a replica of the legitimate one. This is achieved by changing the icon to match the target’s and temporarily disabling the actual add-on via the “chrome.management” API, effectively removing it from the toolbar.
“The polymorphic extension attack is highly effective as it exploits users’ reliance on visual cues for confirmation,” SquareX noted. “In this case, the extension icons on a pinned bar are used to inform users of the tools they are interacting with, making it challenging for them to distinguish between legitimate and malicious extensions.”
These findings come a month after the company disclosed another attack method, called Browser Syncjacking, which enables threat actors to seize control of a victim’s device using a seemingly innocuous browser extension, as reported earlier.