Security experts have discovered a new phishing campaign that utilizes the ClickFix technique to deploy an open-source command-and-control framework known as Havoc.
According to Fortinet ForEGuard Labs, “the threat actor conceals each malware stage behind a SharePoint site and employs a modified version of Havoc Demon in conjunction with the Microsoft Graph API to obscure C2 communications within trusted, well-known services,” as stated in a technical report shared with The Hacker News.
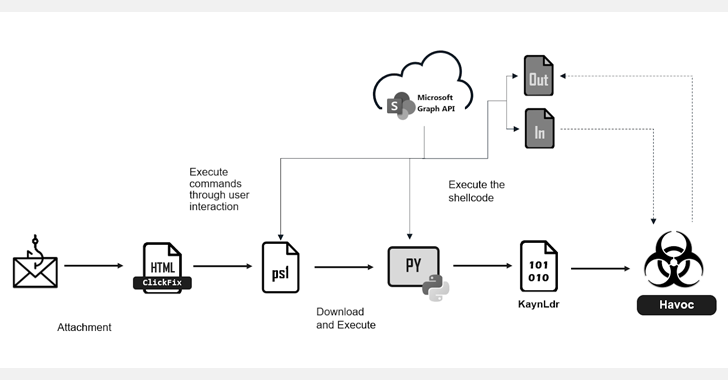
The attack begins with a phishing email containing an HTML attachment (“Documents.html”) that, when opened, displays an error message. This error message uses the ClickFix technique to deceive users into copying and executing a malicious PowerShell command into their terminal or PowerShell, thereby triggering the next stage of the attack.
The command is designed to download and execute a PowerShell script hosted on an adversary-controlled SharePoint server. The newly downloaded PowerShell checks if it’s being run within a sandboxed environment before proceeding to download the Python interpreter (“pythonw.exe”), if it’s not already present in the system.
The next step involves fetching and executing a Python script from the same SharePoint location that serves as a shellcode loader for KaynLdr, a reflective loader written in C and ASM that’s capable of launching an embedded DLL, in this case, the Havoc Demon agent on the infected host.
Fortinet explained that “the threat actor uses Havoc in conjunction with the Microsoft Graph API to conceal C2 communication within well-known services.” The framework supports features to gather information, perform file operations, as well as carry out command and payload execution, token manipulation, and Kerberos attacks.
Meanwhile, Malwarebytes revealed that threat actors are continuing to exploit a known loophole in Google Ads policies to target PayPal customers with bogus ads served via advertiser accounts that may have been compromised.