NVIDIA Container Toolkit Vulnerability: A Bypass for a Now-Patched Security Vulnerability
February 12, 2025
By Ravie Lakshmanan
A new vulnerability has been discovered in the NVIDIA Container Toolkit that could be exploited to break out of a container’s isolation protections and gain complete access to the underlying host. The vulnerability, tracked as CVE-2025-23359 (CVSS score: 8.3), affects all versions up to and including 1.17.3 and has been fixed in version 1.17.4.
The Vulnerability
The vulnerability is a Time-of-Check Time-of-Use (TOCTOU) vulnerability in the NVIDIA Container Toolkit for Linux, which can be exploited when used with default configuration. A crafted container image can gain access to the host file system, allowing an attacker to execute code, deny service, escalate privileges, disclose information, and tamper with data.
Impact
The vulnerability enables bad actors to mount the host’s root file system into a container, granting them unfettered access to all files. Furthermore, the access can be leveraged to launch privileged containers and achieve full host compromise via the runtime Unix socket.
Analysis
Security researchers from Wiz analyzed the container toolkit and found that the file paths used during mount operations could be manipulated using a symbolic link, allowing an attacker to mount from outside the container into a path within "/usr/lib64".
Recommendations
To mitigate the risk, users of the NVIDIA Container Toolkit are recommended to:
- Update to the latest version
- Not disable the
--no-cntlibsflag in production environments
Related Vulnerability
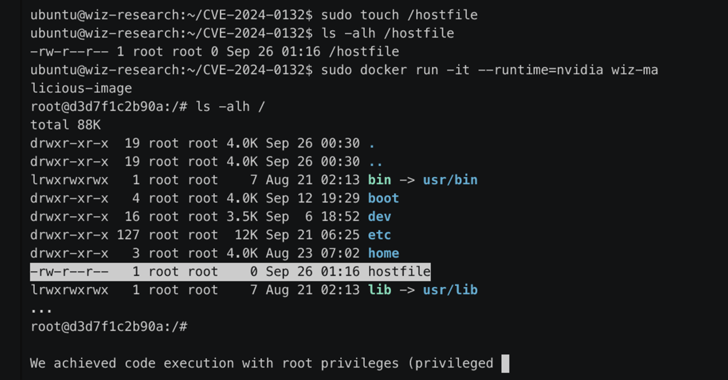
The vulnerability is a bypass for another vulnerability, CVE-2024-0132 (CVSS score: 9.0), which was addressed by NVIDIA in September 2024.
Conclusion
The NVIDIA Container Toolkit vulnerability highlights the importance of keeping software up-to-date and being cautious when using default configurations. By following the recommended steps, users can minimize the risk of exploitation and ensure the security of their containers.
Stay Informed
Follow us on Twitter and LinkedIn to read more exclusive content we post.
Source Link