Ukraine’s Cybersecurity Agency Warns of Fake AnyDesk Connection Requests
Date: January 21, 2025
Author: Ravie Lakshmanan
Malware / Cyber Threat
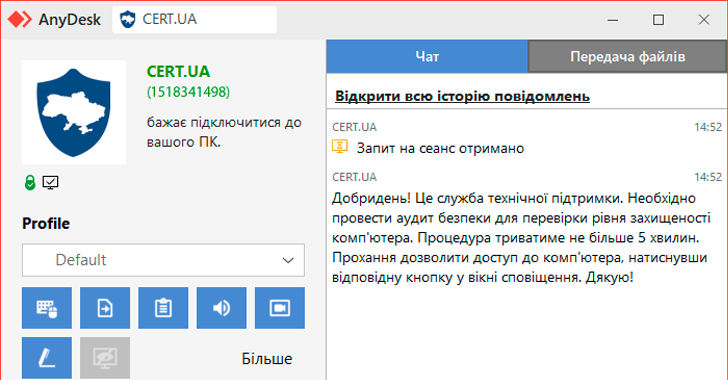
The Computer Emergency Response Team of Ukraine (CERT-UA) has issued a warning about ongoing attempts by unknown threat actors to impersonate the cybersecurity agency by sending AnyDesk connection requests. These requests claim to be for conducting an audit to assess the "level of security," but they are actually part of a social engineering attempt to exploit user trust.
Understanding the Threat
CERT-UA has clarified that it may use remote access software such as AnyDesk in certain circumstances, but only after prior agreement with the owners of affected systems. However, these actions are taken to deliver a remote access trojan known as Ozone, which can grant remote access to infected Windows systems.
Sticky Werewolf: A Pro-Ukrainian Cyberspy Group
CERT-UA has also described Sticky Werewolf as a pro-Ukrainian cyberspy group that mainly targets state institutions, research institutes, and industrial enterprises in Russia. However, a previous analysis from Israeli cybersecurity company Morphisec has raised uncertainty about this connection.
Other Threat Activity Clusters
Other threat activity clusters targeting Russian entities in recent months include Core Werewolf, Venture Wolf, and Paper Werewolf (also known as GOFFEE). These groups have been observed using various tactics, including leveraging a malicious IIS module called Owowa to facilitate credential theft.
Conclusion
The success of these attacks is not yet known. It is essential for organizations to be aware of these social engineering attempts and to exercise caution when receiving AnyDesk connection requests. By staying informed and vigilant, individuals and organizations can protect themselves against these types of threats.
Follow Us
If you found this article interesting, follow us on Twitter and LinkedIn to read more exclusive content we post.