Global Botnet Utilizes Hijacked MikroTik Routers to Propagate Malware via Spam Campaigns
A Growing Concern in the Cybersecurity World
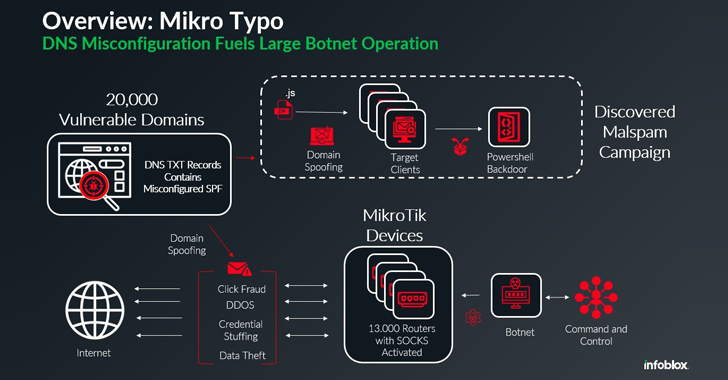
A global network of approximately 13,000 hijacked MikroTik routers has been employed as a botnet to propagate malware via spam campaigns, according to the latest addition to a list of botnets powered by MikroTik devices.
Exploiting Misconfigured DNS Records
The activity "takes advantage of misconfigured DNS records to pass email protection techniques," Infoblox security researcher David Brunsdon said in a technical report published last week. "This botnet uses a global network of Mikrotik routers to send malicious emails that are designed to appear to come from legitimate domains."
The DNS Security Company’s Analysis
The DNS security company, which has codenamed the campaign "Mikro Typo," said its analysis sprang forth from the discovery of a malspam campaign in late November 2024 that leveraged freight invoice-related lures to entice recipients into launching a ZIP archive payload.
Exploiting ZIP Archives and PowerShell Scripts
The ZIP file contains an obfuscated JavaScript file, which is then responsible for running a PowerShell script designed to initiate an outbound connection to a command-and-control (C2) server located at the IP address 62.133.60[.]137.
Vulnerabilities in MikroTik Firmware
The exact initial access vector used to infiltrate the routers is unknown, but various firmware versions have been affected, including those vulnerable to CVE-2023-30799, a critical privilege escalation issue that could be abused to achieve arbitrary code execution.
SOCKS Proxies and Enhanced Malicious Activity
"Regardless of how they’ve been compromised, it seems as though the actor has been placing a script onto the [Mikrotik] devices that enables SOCKS (Secure Sockets), which allow the devices to operate as TCP redirectors," Brunsdon said.
Elevated Concerns
Enabling SOCKS effectively turns each device into a proxy, masking the true origin of malicious traffic and making it harder to trace back to the source. The lack of authentication required to use these proxies allows other threat actors to weaponize specific devices or the entire botnet for malicious purposes, ranging from distributed denial-of-service (DDoS) attacks to phishing campaigns.
Exploiting SPF Records
The malspam campaign in question has been found to exploit a misconfiguration in the sender policy framework (SPF) TXT records of 20,000 domains, giving the attackers the ability to send emails on behalf of those domains and bypass various email security protections.
Recommendations for MikroTik Device Owners
MikroTik device owners are recommended to keep their routers up-to-date and change default account credentials to prevent any exploitation attempts.
Conclusion
"With so many compromised MikroTik devices, the botnet is capable of launching a wide range of malicious activities, from DDoS attacks to data theft and phishing campaigns," Brunsdon said. "The use of SOCKS4 proxies further complicates detection and mitigation efforts, highlighting the need for robust security measures."
Stay informed about the latest cybersecurity threats and trends by following us on Twitter and LinkedIn.
Source Link